
三星Android设备通过MTP(Media Transfer Protocol )任意文件读写漏洞PoC(SVE-2017-10086)
https://github.com/smeso/MTPwn
浏览器里运行的C语言环境:可将C++编译为WebAssembly格式在浏览器运行
https://tbfleming.github.io/cib/
https://github.com/tbfleming/cib
从微信小程序看前端代码安全
https://share.whuboy.com/weapp.html
34c3 Web部分Writeup
https://lorexxar.cn/2018/01/02/34c3-writeup/
“Inside Intel Management Engine” about activation JTAG for IntelME
https://github.com/ptresearch/IntelME-JTAG/blob/master/Inside_Intel_Management_Engine.pdf
用Golang写的域名信息搜集工具
https://github.com/tomsteele/blacksheepwall
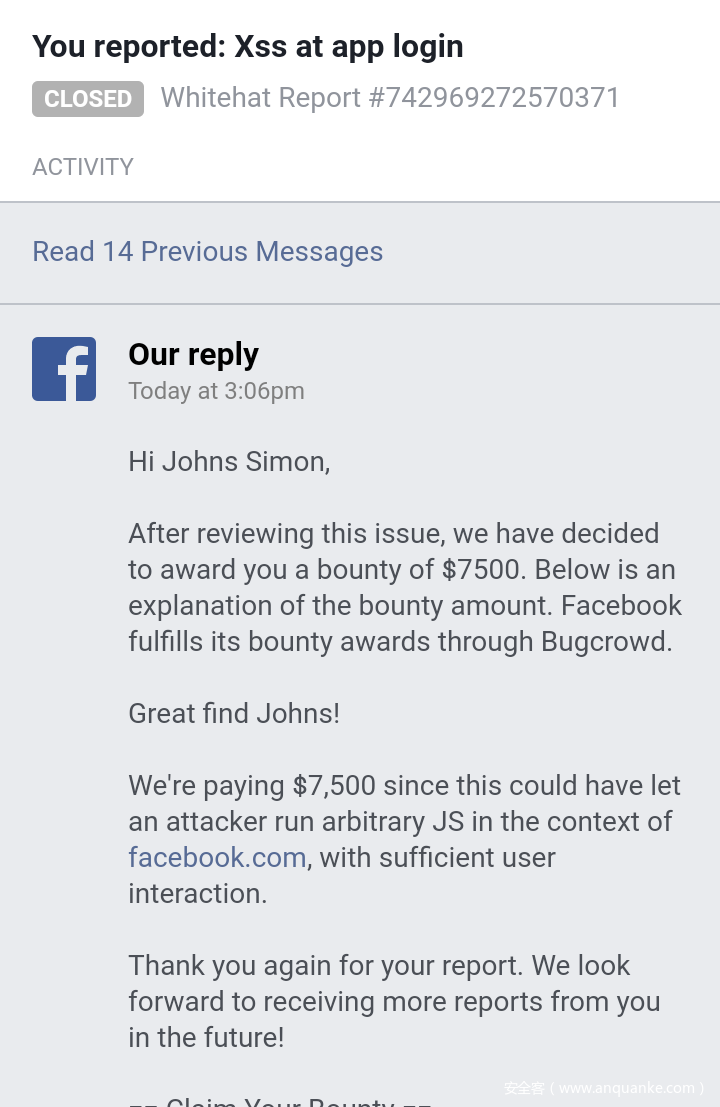
facebook移动站(m.facebook.com)上的DOM型XSS writeup,官方确认后给了$7500作为奖励
https://thesecurityexperts.wordpress.com/2017/12/20/dom-xss-in-facebook-mobile-siteapp-login/
phpMyAdmin < 4.7.7 CSRF漏洞
https://thehackernews.com/2018/01/phpmyadmin-hack.html
http://securityaffairs.co/wordpress/67243/hacking/phpmyadmin-csrf-vulnerability.html
phpMyAdmin 官方公告
https://www.phpmyadmin.net/security/PMASA-2017-9/
gron:使JSON greppable的工具
▶ gron "https://api.github.com/repos/tomnomnom/gron/commits?per_page=1" | fgrep "commit.author" json[0].commit.author = {};
json[0].commit.author.date = "2016-07-02T10:51:21Z";
json[0].commit.author.email = "mail@tomnomnom.com";
json[0].commit.author.name = "Tom Hudson";https://github.com/tomnomnom/gron
脱壳反编译PyInstaller恶意软件
https://www.youtube.com/watch?v=x8OtmBoCyw4
免root使用frida
https://koz.io/using-frida-on-android-without-root/
CVE-2017-5129:Google Chrome “ScriptProcessorHandler::FireProcessEvent()” Use-after-free 漏洞
https://bugs.chromium.org/p/chromium/issues/detail?id=765495
作者:安全客小编2
如若转载,请注明出处: https://www.anquanke.com/post/id/93210